Often customers want to see the ease of use of VMware NSX distributed IDS/IPS. But to demonstrate its capabilities it might be necessary to setup tools like metaspoit and vulnerable software versions. With idsreplay I’ve created an easy way to run you IDS/IPS Demo “out-of-the-box” without the need to setup & configure potentially dangerous software in a customer environment.
idsreplay comes in a pre-packaged virtual appliance / vapp format but is also available as container image, pre-compiled binary and source code. All available here https://github.com/danpaul81/idsreplay
How it works
idsreplay takes network traffic patterns from IDS signature files (suricata 4 format) and “replays” them to a target system. Every IDS/IPS also leveraging these signatures should then generate alerts. This post focuses on NSX-T distributed IDS/IPS but I’ve also successfully demoed NSX Advanced Load Balancer WAF (a.k.a AVI Networks). Let me know if you successfully tried other IDS/IPS implementations.
How to run
1. Prepare NSX
You should have a NSX environment up & running. Its not necessary to have overlay networking enabled.
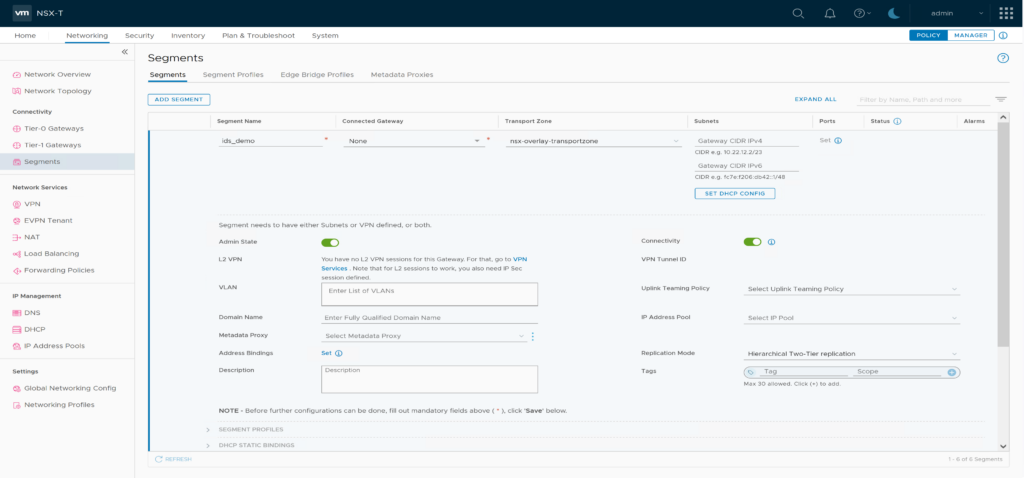
Create NSX Segment “ids_demo” in overlay or vlan transport zone. No Gateway connection / Subnets needed.
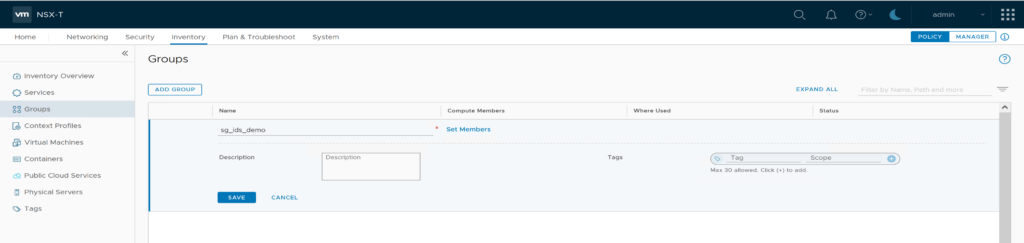
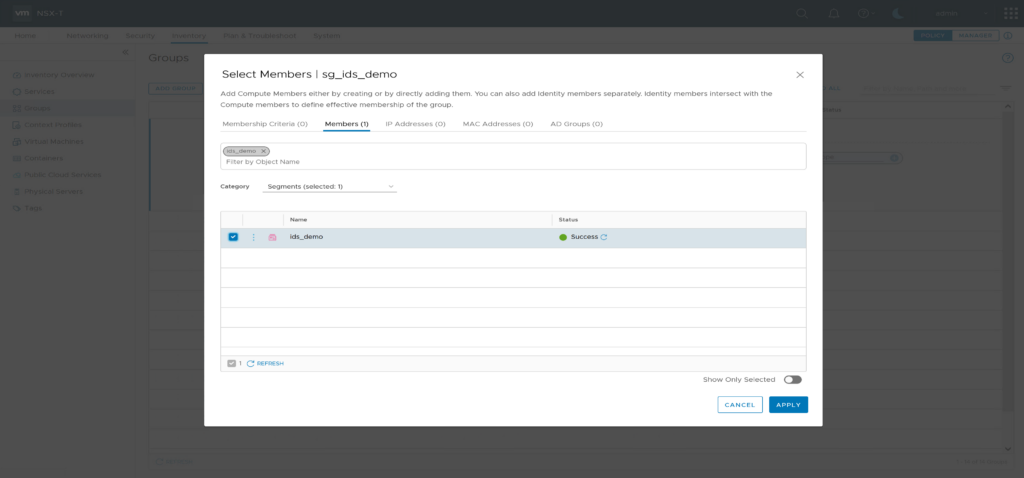
Prepare a security group “sg_ids_demo” and add the segment “ids_demo” as member.
Enable NSX IDS/IPS for your compute cluster and update signatures.
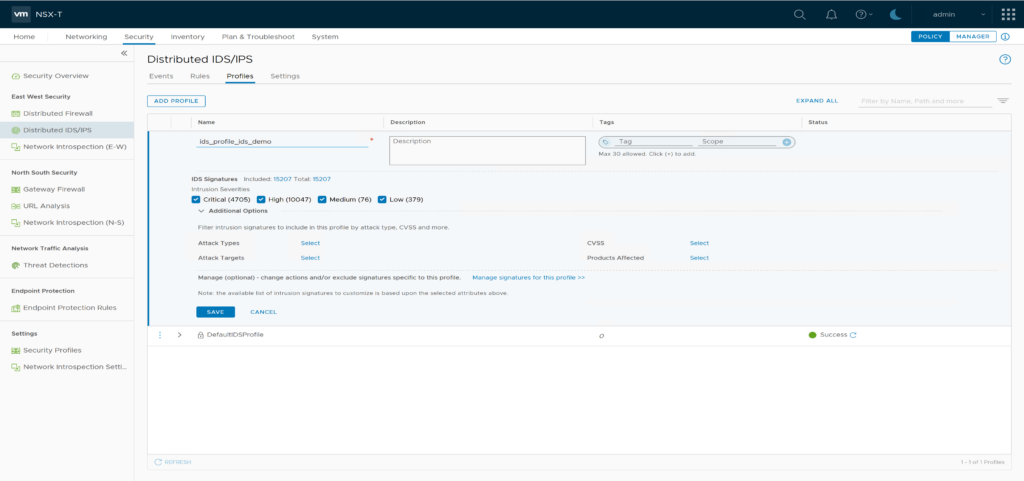
Create a new IDS Profile “ids_profile_ids_demo” and leave all default settings
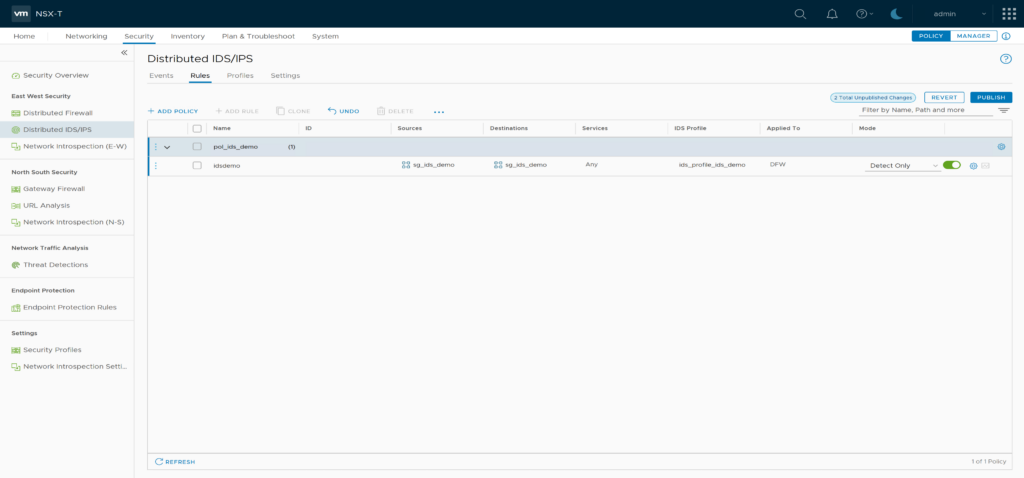
Create a new IDS/IPS Policy “pol_ids_demo” and add a rule “idsdemo” with source and destination “sg_ids_demo” and profile “ids_profile_ids_demo”. Set mode to “Detect Only” and don’t forget to publish the changes.
2. Deploy idsreplay vApp
Download the latest vApp Appliance https://github.com/danpaul81/idsreplay/releases/latest
Deploy idsreplay vApp ovf template on the NSX IDS enabled Compute Cluster. As VM Network select Segment “ids_demo”. Leave all default settings on “Customize Template”. Hint: vCenter DRS should be enabled to deploy a vApp
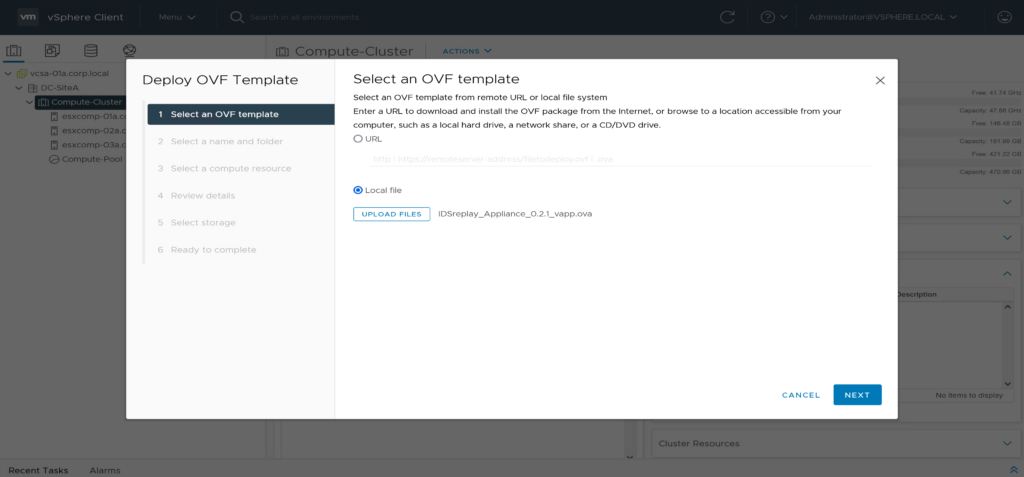
select ovf template 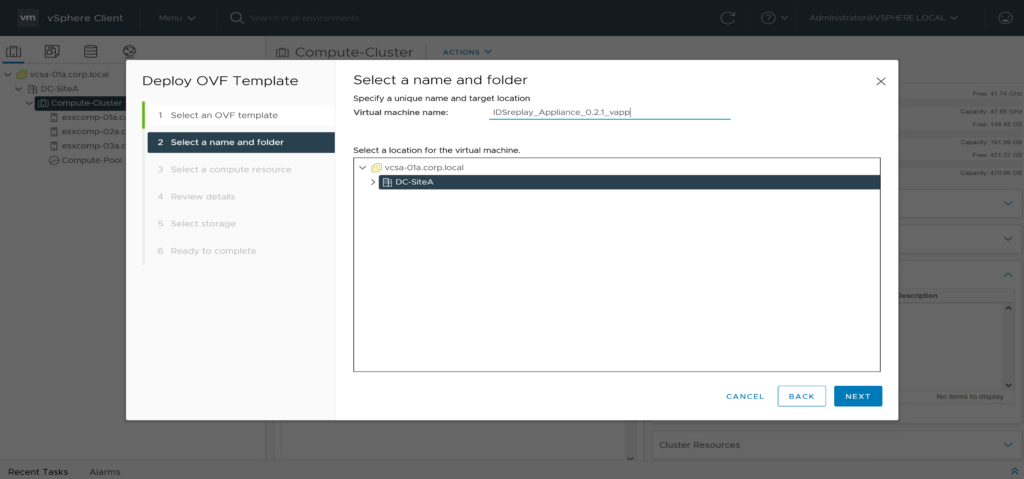
select name/folder 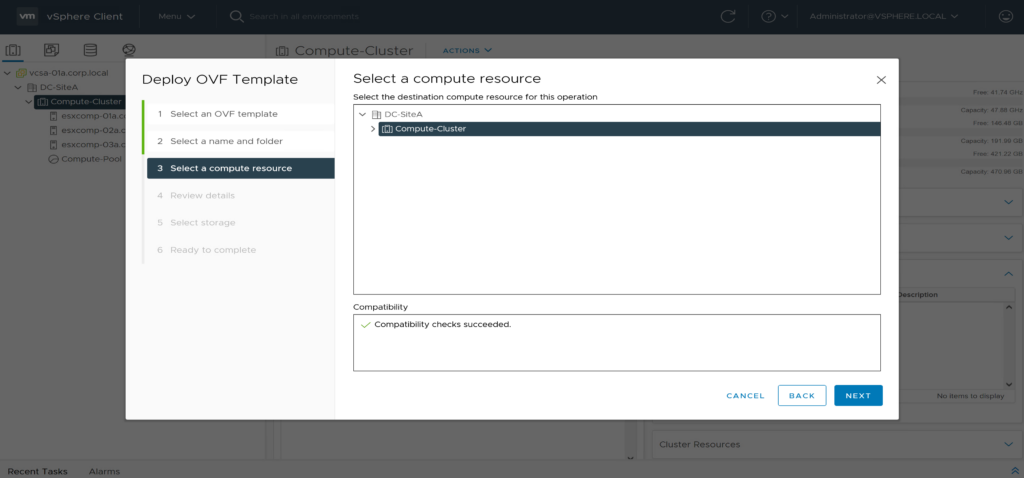
select compute ressource 
review details 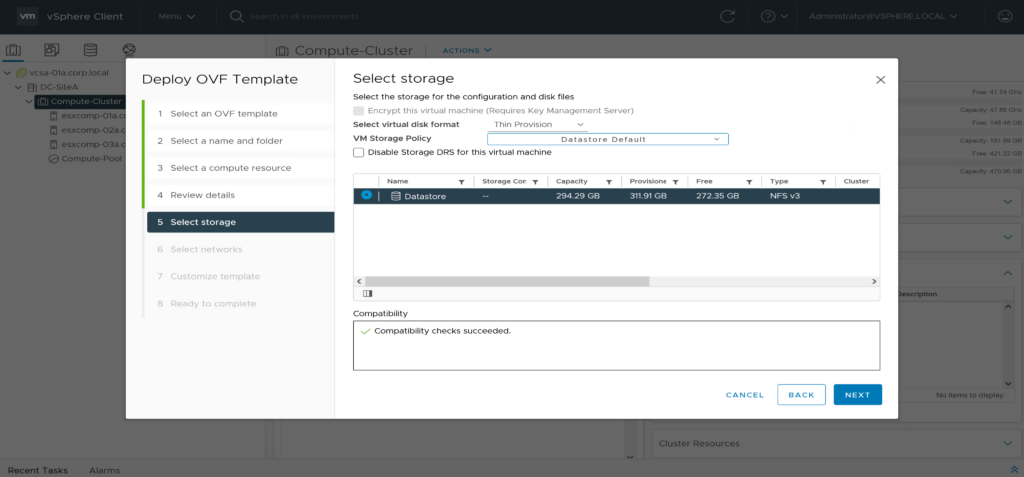
select storage 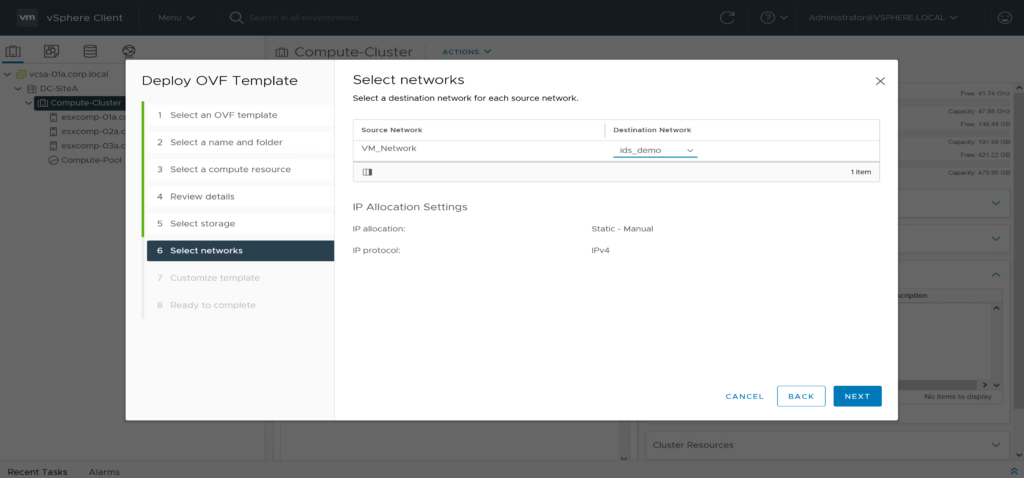
select networks 
customize template 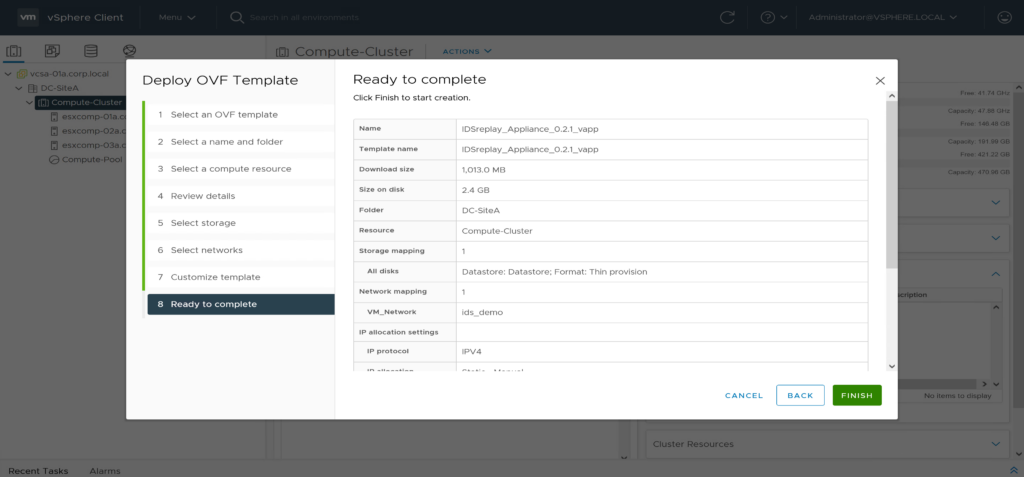
ready to complete
After successful deployment you can Power On the IDSreplay Appliance vApp. It contains two VMs wich will be started and configured automatically.
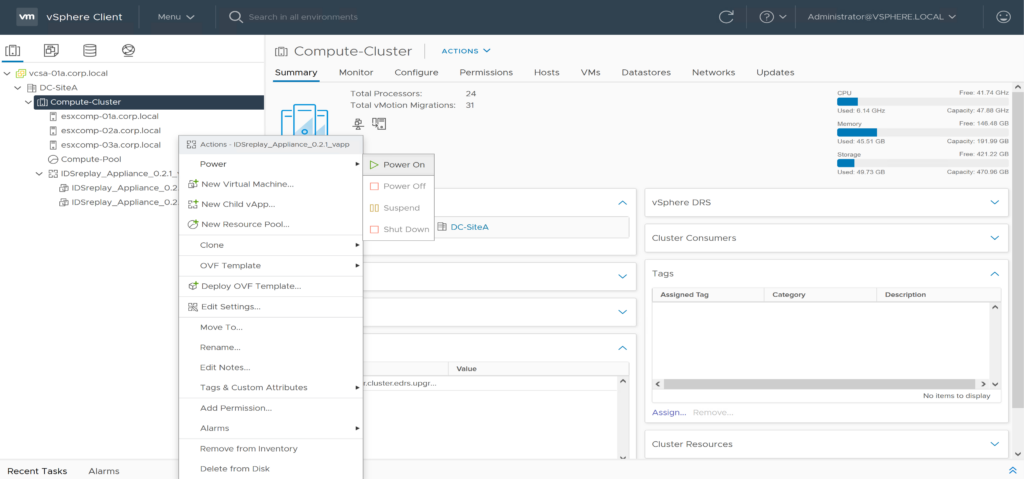
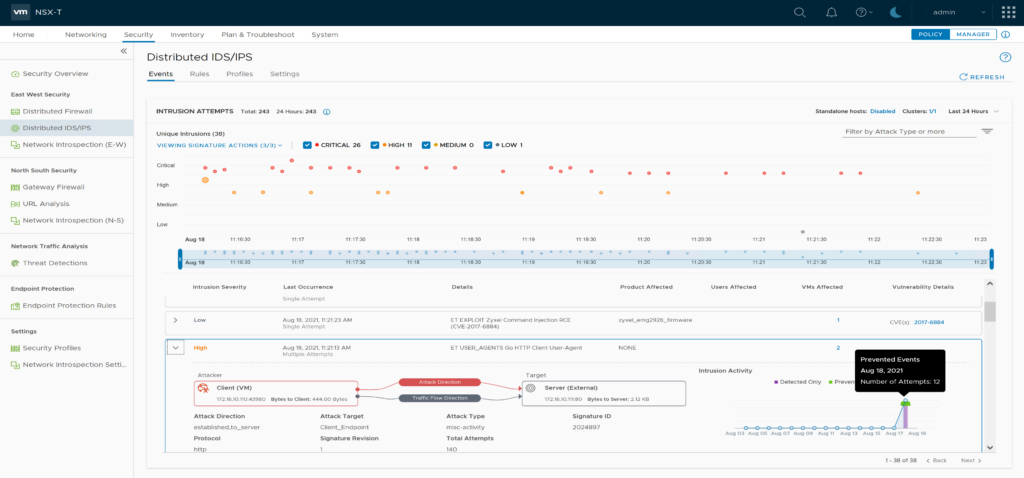
3. Check NSX IDS/IPS Events
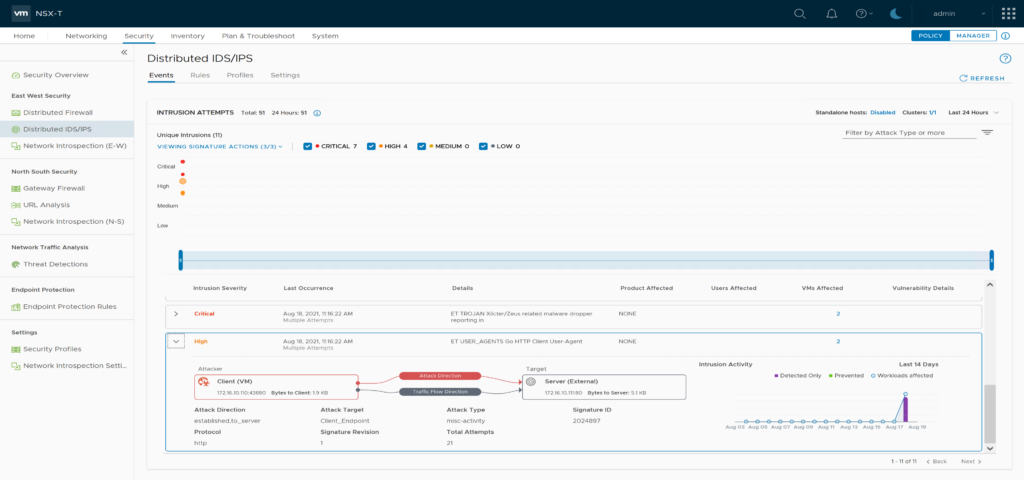
After some minutes NSX IDS/IPS should show intrusion attempts on the Events Screen. You can now browse and investigate them.

4. (optional) Demo intrusion prevention Mode (IPS)
idsreplay uses golang http libraries to run the replay. Most of the requests use the HTTP User Agent “Go HTTP Client User Agent” which also causes an IDS event. To demonstrate intrusion prevention mode you can block these requests.
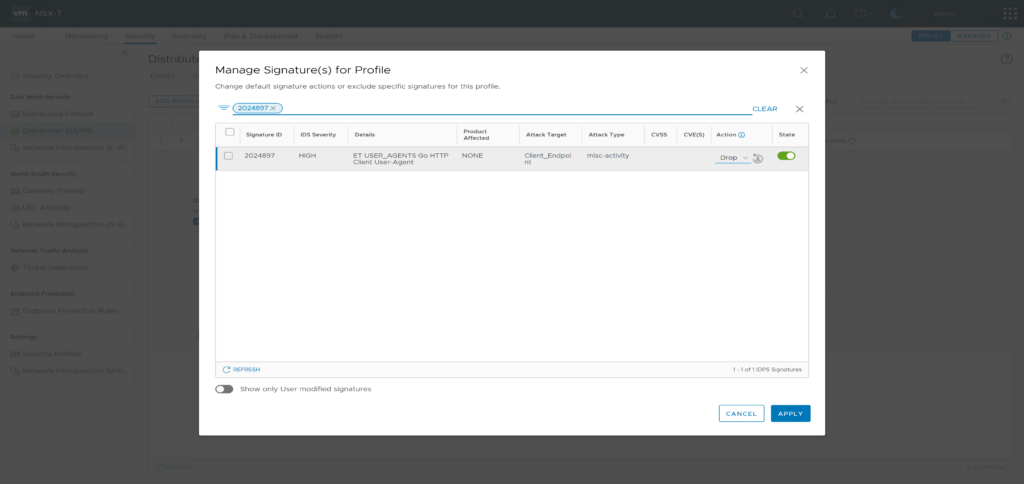
Find “ET USER_AGENTS Go HTTP Client User-Agent” in the events list and note its Signature ID [2024897]
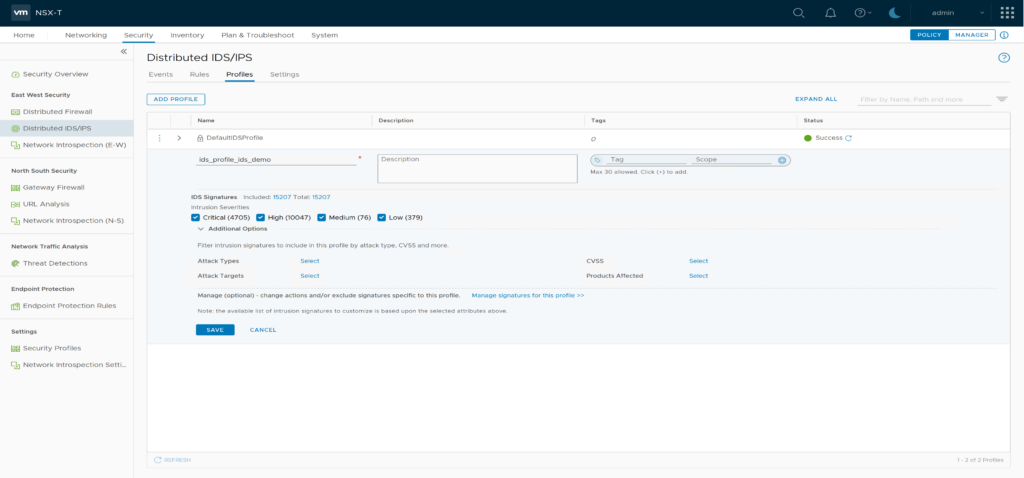
Edit “ids_profile_ids_demo”, click on “Manage signatures for this profile” and search for signature ID 2024897. Now set the signature Action to “Drop”, and Apply the changes.
Go to the “idsremo” IDS Rule and change Mode to “Detect & Prevent”. Don’t forget to publish the changes.
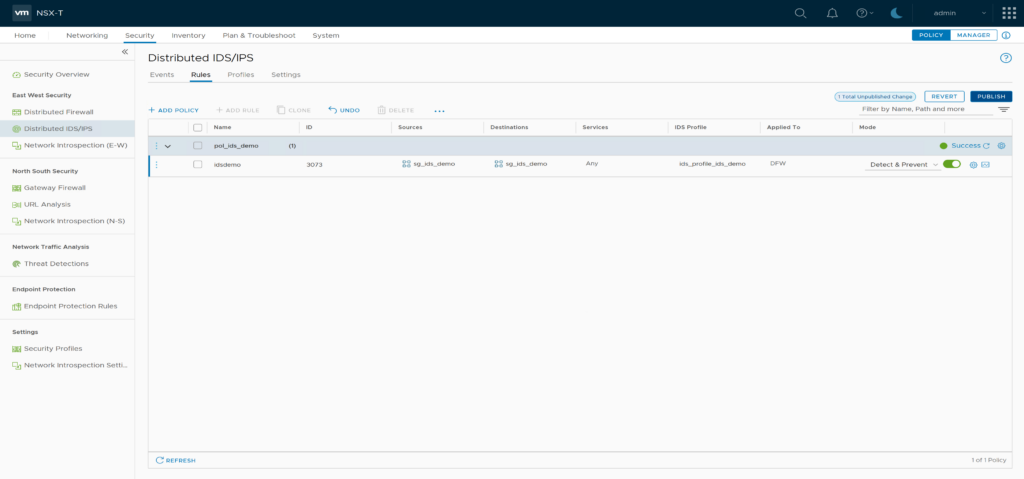
After 2-3 Minutes you should Refresh the IDS/IPS Events screen and re-check the “ET USER_AGENTS Go HTTP Client User-Agent” for prevented Events.