VMware recently introduced a new solution Aria Guardrails which allows for central policy management and desired state configuration in public clouds. With this you e.g. could automatically enforce a password policy in your public cloud accounts without touching every account and monitoring it manually for drifts. The product so far has only been able to work in “monitoring” mode which means that it was able to detect drifts compared to defined policies, but it has not been able to remediate. This has changed recently where in the June 2023 update “enforcement mode” was introduced. To use enforcement mode the integrated accounts do require “elevated access” configuration which allows for proper user permissions on public cloud to execute commands. It supports the concept of having low permissions for the discovery parts while having a very defined role for execution of actions.
This blog describes how to configure elevated access as its default wizard does not cover all specifics.
Create Policy in AWS
Elevated Access requires a specific role in AWS where custom policies are attached. The creation of this role and the related policies is automatically done by a script provided by VMware as described in the account management wizard in Guardrails.
To allow for proper script execution, however some pre-requisites must be done. One is the configuration of a policy that allows the script to create roles and policies.
- Go to your AWS console and navigate to the IAM section.
- In the IAM section go to policies and create a new policy
- Select “IAM” in the policy wizard
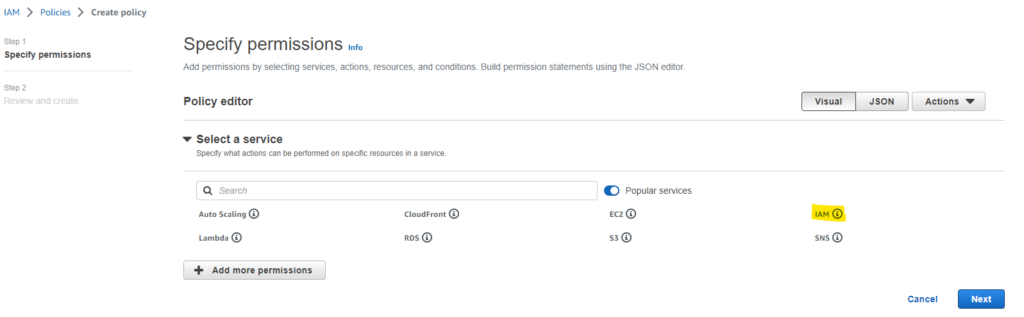
- In the following screen select the permissions under “access level” as per below specification:
- Section List: ListPolicies
- Section Write: CreateRole
- Section Permissions Management: AttachRolePolicy
- Section Permissions Management: CreatePolicy
- Specify a policy name like “AriaCreateRole” and create the policy
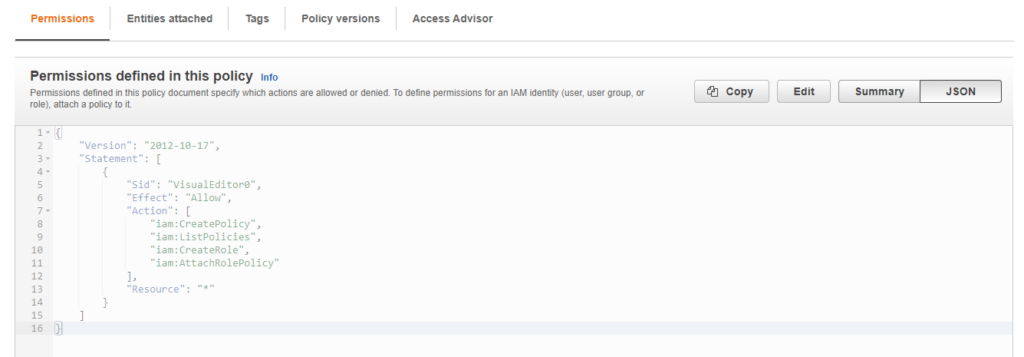
The final policy should have below permissions
Create Role in AWS
The next step is to create a role related to the policy.
- Navigate to roles in the IAM section
- Create a new role of type “AWS account”
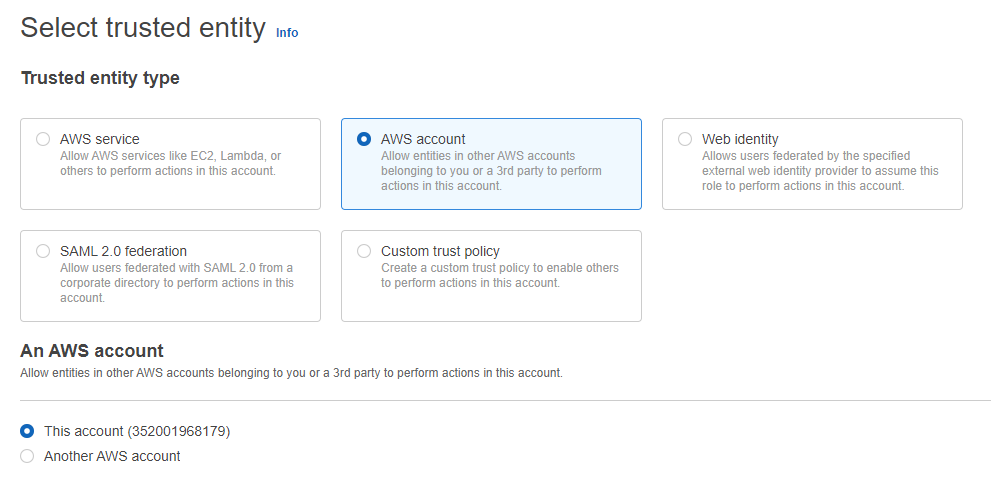
- Specify a role name like “AriaRoleforElevatedAccess” and create it.
- The final role should have below trust relationships
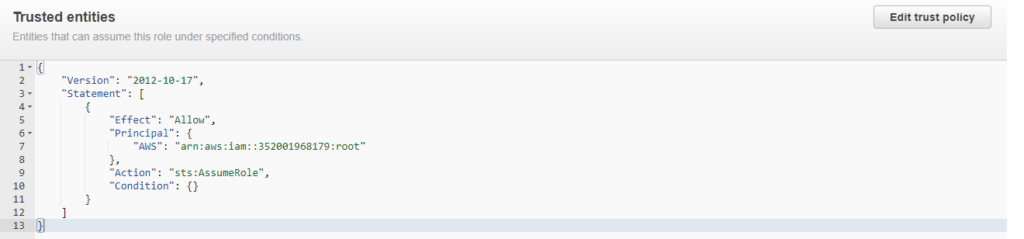
Run the script for elevated access
Now it’s time to run the script as suggested in the Guardrails account wizard. The easiest way to execute it is through the AWS CloudShell as it handles authentication automatically.
Copy the command from Guardrails “Configure Elevated Access” wizard into AWS CloudShell and make sure the previously created role name is attached to the command:
curl https://api.mgmt.cloud.vmware.com/aria/data/management-endpoint/scripts/AWS/elevated-credentials/aws_account_security_policies_and_roles.sh --output aws_account_security_policies_and_roles.sh && bash aws_account_security_policies_and_roles.sh ############,########-####-####-####-############,AriaRoleforElevatedAccessAfter successful execution you should find a new role in AWS Console with name “VMwareAriaHubElevatedAccess”.
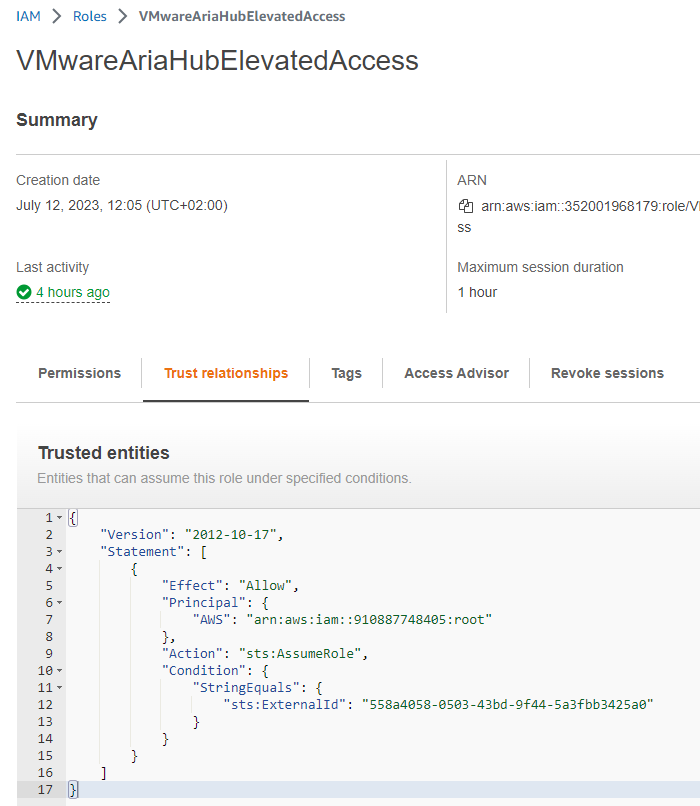
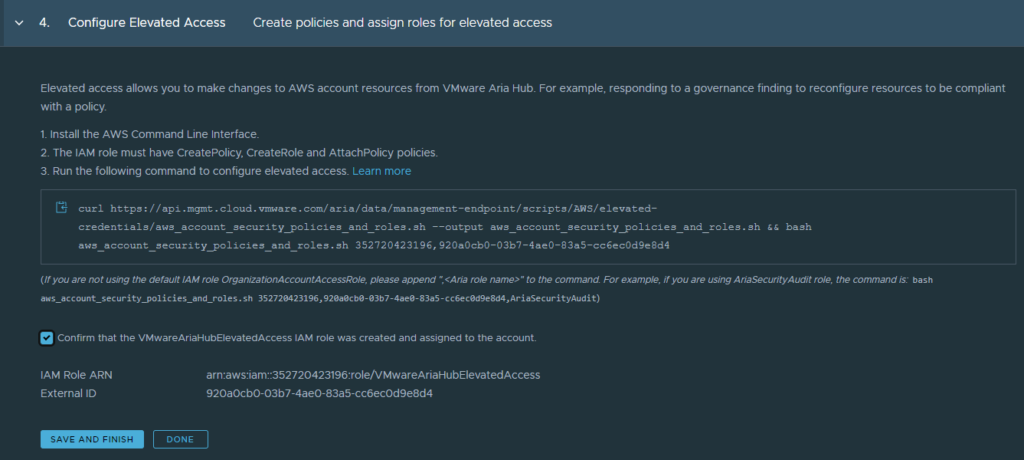
Enable Elevated Access in Guardrails
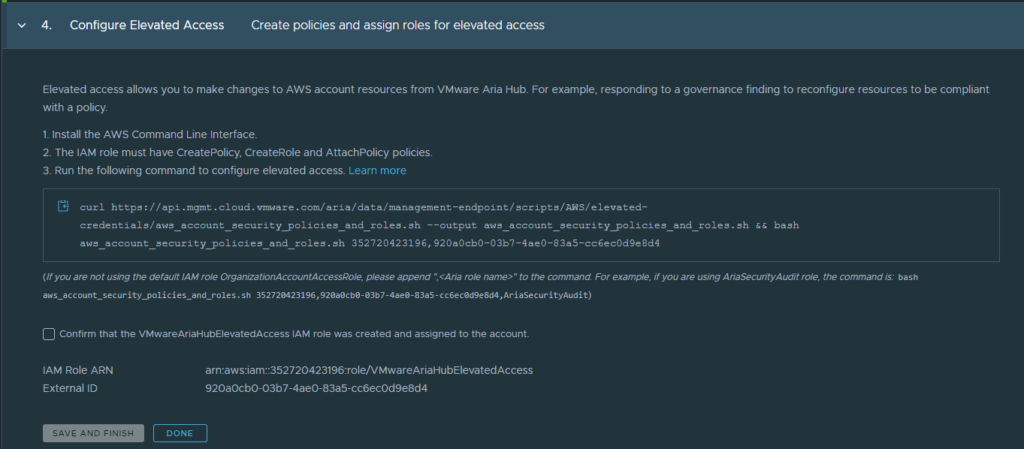
If all prerequisites have been executed, you can safely check the checkbox in the Guardrails wizard and “save and finish” to enable elevated access.
If this has been successful, you should see a hook in the elevated access column of the cloud account.
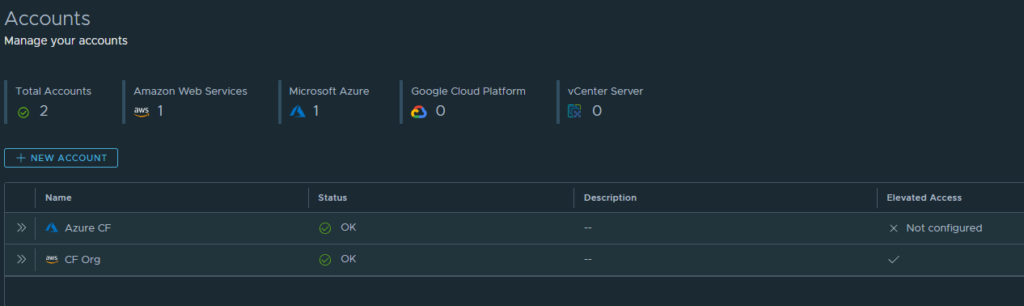
After that Guardrails desired states can be executed in “enforcement” mode.
Please note: As of June 2023, enforcement is only supported for templates that are defined on org level. If did assign a template to a specific project, the enforcement option will be greyed out.
Have fun!
- 1-node Kubernetes Template for CentOS Stream 9 in VCF Automation - 30. September 2024
- Aria Automation custom resources with dynamic types - 9. August 2024
- Database-as-a-Service with Data Services Manager and Aria Automation - 4. July 2024
